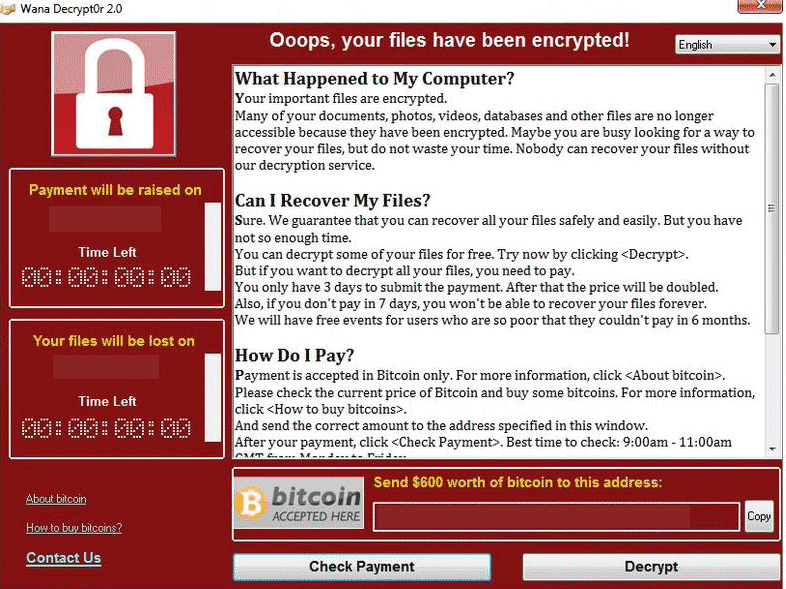
En un post realizado en el Blog de internos de Microsoft, twiteado por Snowden, el ingeniero Brad Smith cuenta que el malicioso WannaCrypt que pide Bitcoins por soltar el secuestro de los archivos de su computador afectando hasta Hospitales, fué reportado como robado en Marzo por la Agencia Nacional de Seguridad de los Estados Unidos. Lee más aquí y también como removerlo.
Starting first in the United Kingdom and Spain, the malicious “WannaCrypt” software quickly spread globally, blocking customers from their data unless they paid a ransom using Bitcoin. The WannaCrypt exploits used in the attack were drawn from the exploits stolen from the National Security Agency, or NSA, in the United States. That theft was publicly reported earlier this year. A month prior, on March 14, Microsoft had released a security update to patch this vulnerability and protect our customers. While this protected newer Windows systems and computers that had enabled Windows Update to apply this latest update, many computers remained unpatched globally. As a result, hospitals, businesses, governments, and computers at homes were affected.
All of this provides the broadest example yet of so-called “ransomware,” which is only one type of cyberattack. Unfortunately, consumers and business leaders have become familiar with terms like “zero day” and “phishing” that are part of the broad array of tools used to attack individuals and infrastructure. We take every single cyberattack on a Windows system seriously, and we’ve been working around the clock since Friday to help all our customers who have been affected by this incident. This included a decision to take additional steps to assist users with older systems that are no longer supported. Clearly, responding to this attack and helping those affected needs to be our most immediate priority.
Aquí te dejamos varias soluciones:
start – control panel – windows firewall – Inbound Rules – New Rule – port – next – Specific local ports – 135,137,138,139,445 – Block The connection- next – next – name (block) – Finish
Descargar éste tool de Symantec:
https://www.symantec.com/connect/sites/default/files/SMB2%20Toggle%20Too.zip